Here’s The Dirty Truth About Crypto Wallet Security
We’ve all heard the jaw-dropping news about NFTs sold in the last few years. Extraordinary prices, sometimes ugly art, and often nameless buyers and sellers.
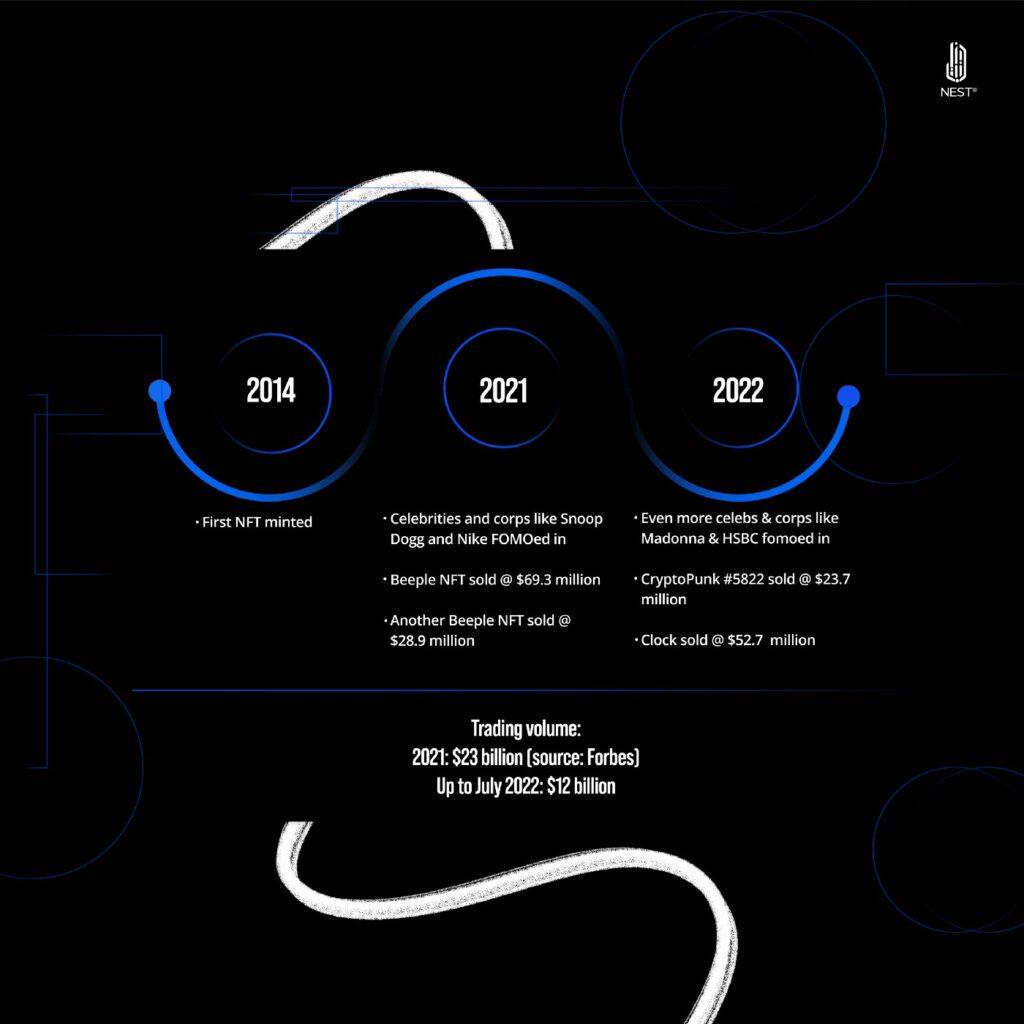
With the NFT market’s continuous upward trajectory, NFT platforms and owners have become the new prey for (cyber) criminals. Bad actors use a myriad of techniques to steal NFTs. Here’s a quick overview of the most often used ways to steal your NFTs (ugly or not).
2-Factor Authentication: the good, the bad, and the ugly
According to recent analytic reports, many NFT investors skip two-factor authentication (2FA). Segway: even if you don’t skip it, 2FA isn’t as secure as it’s made out to be. Plus, it’s annoying. But 2FA, right now, is the standard among most organizations — your bank, the government, et cetera et cetera. We’ll give it some credit since hackers have to jump through one more hoop to get you.
Back to the subject, by skipping 2FA, hackers can breach NFT marketplace accounts more easily. Take Nifty Gateway, for example. Several people had their accounts wiped out and hundreds of thousands of dollars worth of NFTS stolen. And guess what? Nifty says users were to blame because they neglected two-factor authentication.
The same thing happened with OpenSea. Users lost millions in NFT theft — Bored Apes, Mutant Apes, Decentraland assets, and more. To add fuel to the fire, OpenSea’s CEO disclosed that only $1.7 million worth of assets were stolen, but after other parties joined in the calculation, it was found that the heist amounted to $200 million. It was a whole back and forth of throwing blame where OpenSea said that their website’s code wasn’t compromised and instead, the hacker used a phishing technique. Users insisted they never clicked on any links, so who knows?
Phishing: the good, the bad, and the ugly
Maybe just the bad and the ugly for this one — Phishing is another popular method criminals use. Victims are usually manipulated into giving up their credentials through fraudulent emails or websites designed to resemble the user’s NFT wallet. Usually, you’ll receive an email that looks legit, which then asks you to click on a link. This link takes you to a malicious website, where you’re directed to enter your credentials.
Many users are now careful not to fall for phishing scams, but as always, scammers are perpetually looking to up their game and create more advanced techniques. For example, victims receive a free NFT as a gift. Accepting the gift exposes the NFT holders to the risks of compromising their wallet. The structure of current mainstream wallets and NFT marketplaces shows significant shortcomings of pseudo-anonymous solutions. And by that, we mean using lengthy combinations of numbers and letters to mask user identities. This does not provide real-world ownership authentication nor true anonymity. They are, by design, insufficient toolsets to safeguard assets in crypto wallets.
So, Does Your Current Wallet Protect You? (Hint: NOPE)
It is commonly believed that crypto wallets are unhackable due to blockchain’s sophisticated cryptographic technology. But why do we keep seeing news about users losing their fortune in hack attacks? Because blockchain is simply an immutable ledger, a mathematical proof that an event happened. It does not provide recognized assurance that you own a certain asset.
MetaMask is the world-leading wallet for storing digital assets like cryptocurrencies and NFTs. Its users haven’t been spared.
In April this year, $650,000 worth of NFTs were drained from a single MetaMask wallet. The victim, Domenic Iacovone, tweeted, “Got a phone call from Apple, literally from Apple (on my caller Id) called it back because I suspected fraud and it was an Apple number, so I believed them, they asked for a code that was sent to my phone and two seconds later my entire MetaMask was wiped.” (Well, here’s an ad for an android phone if we’ve ever seen one ;0) )
Another MetaMask phishing scam involves an email impersonating MetaMask, asking users to verify their wallets. This leads to a fraudulent website that looks EXACTLY (and we repeat EXACTLY) like the real authentic MetaMask site, and victims are asked to provide their recovery phrase. As we all know, once the information is provided, it’s game over. (As the real Metamask states: “We will never ever ever ask you for your recovery phrase” Take note!).
While the NFT technology is used to generate proof of authenticity and ownership on the blockchain, data and assets are assigned to wallet addresses, not to the users.
If you (accidentally) reveal your wallet’s private key to others, either in a phishing scam or other forms of hacks (or just because you’re of the sharing nature), the holder of your key becomes the owner of the data and ALL the assets inside that wallet. Current NFT wallets can (but often don’t) compensate victims but are unable to recover the user’s assets for them.
What’s the solution then? We hear you ask.
Let’s simplify. Digital assets (like NFTs) are held in blockchain wallet addresses (essentially a long sequence of letters/numbers). These digital assets are not owned by the user, as detailed earlier. Instead, they are merely assigned to wallet addresses which users access. Because of this, a user’s ownership of an NFT cannot be proven, particularly if there are no systems in place for genuine identification and authentication. In short, once hackers have gotten ahold of your private keys, there is no way to then certify that the assets they now control are rightfully yours — just to bang home this point let’s say Andy owns a Bored Ape which is stored in Metamask wallet address “XOXO” and I steal Andy’s keys — I now own wallet address “XOXO” (Tadaa). Andy can’t prove that he is the rightful owner of the assets and/or the wallet address “XOXO”.
To solve this, NEST® constructed a system to facilitate user-led and user-owned data assets. Self-Sovereign Distributed Identification (SSDID) was developed to solve ownership and provenance problems. With this, users’ digital assets across networks like Ethereum, Binance, Polygon, Solana, and Ava can instantly be secured, owned, authenticated, and controlled by the rightful holder.
With the SSDID, users set their personal, hyper-encrypted digital to real-world identity to confidentially sign, encrypt, transfer and control both their personal information and their digital assets. The personally-secured, distributed environment and personalized, device-side encryption works to actively protect from fraud and hacking, as all transactions across any blockchain network confidentially leverage authentication and provenance through SSDID verification.
NEST® highlights the term ‘distributed’ identification, as it is the only true way to gain genuine ownership control, with regional compliance, in an actually decentralized system. User owned. User controlled. No one except the owner, not even NEST®, can decrypt the users’ encrypted content, reverse engineer who performed which transaction, nor reveal the details of an SSDID.
Digital asset owners (the whole world) need fundamental, real-world protection with personalized encryption, which comes with interoperable choice selection to control digital assets and transactional exchange. NEST® has already embarked on its journey, launching a revolution in confidential distributed control. So long story short, ya might wanna check out how your NEST® will lead towards a practical, trusted, confidential, and decentralized global economy. With NEST® and DLT (a decentralized database managed by various participants), we can choose to define our future